Zero Trust Network Access (ZTNA) has quickly become the cornerstone of modern enterprise cybersecurity. Unlike traditional VPNs, which extend broad network access once authenticated, Zero Trust operates on the principle of “never trust, always verify”—providing continuous, context-aware access to specific applications.
For organizations running virtual desktop infrastructure (VDI) and virtual applications across distributed teams, implementing Zero Trust is more than a technical upgrade; it’s a strategic necessity. By enforcing granular access controls, continuous authentication, and application isolation, enterprises can better protect sensitive data, improve performance, and comply with regulatory frameworks in an era defined by hybrid work.
The Security Imperative: Why Traditional VPN Models Fall Short
Hybrid work has expanded the cyberattack surface beyond recognition. According to recent data, 84% of organizations reported cyberattacks in 2025, up from 65% in 2024. Home networks, unmanaged BYOD devices, and unsecured access points create vulnerabilities that traditional security models weren’t designed to handle.
Key Weaknesses of VPNs
- Broad Network Access – VPNs open entire network segments, exposing resources far beyond a user’s job role.
- Static Authentication – After login, users are trusted throughout the session, regardless of device posture changes.
- Bottlenecks – VPN concentrators struggle with cloud traffic backhauling, leading to latency and degraded UX.
- Limited Scalability – Hardware VPNs scale poorly as remote workforces grow.
In today’s environment, this “trust but verify” perimeter approach leaves organizations blind to lateral movement and insider threats.
Zero Trust Architecture: Core Principles for Virtual Applications
When organizations shift to delivering applications virtually, securing access becomes a top priority. Traditional perimeter defenses no longer hold up in a world of hybrid workforces, cloud applications, and distributed teams. That’s where Zero Trust Architecture (ZTA) steps in.
At its heart, Zero Trust is built on three core principles: verify explicitly, use least privileged access, and assume breach. Let’s break these down in practical terms for virtual applications.
1. Verify Explicitly
In a Zero Trust model, nothing is taken at face value. Every access request must be authenticated and validated using multiple signals—like user identity, device health, location, and application context.
Think of it as a security checkpoint that doesn’t just scan your ID but also checks if your device is patched, where you’re connecting from, and whether you’re allowed into this specific “room” of the application.
2. Use Least Privileged Access
Access should never be broader than necessary. By applying Just-in-Time (JIT) and Just-Enough-Access (JEA) controls, users get only the permissions they need, exactly when they need them.
For example, a contractor might get temporary access to one app for a project, instead of permanent access to the entire environment. This reduces risk and keeps the attack surface tight.
3. Assume Breach
Finally, Zero Trust designs systems with the mindset that attackers might already be inside. The goal is to minimize damage if that happens. Techniques like end-to-end encryption and micro-segmentation ensure that even if one area is compromised, the threat cannot easily spread across the network.
It’s like sealing off rooms in a building—if one door is forced open, the intruder can’t roam freely everywhere else.
Why It Matters for Virtual Applications
Virtual apps are often the backbone of critical workflows, from secure remote desktops to SaaS platforms. Applying Zero Trust principles here ensures organizations can deliver these apps to any device, anywhere, without sacrificing security or usability.
ZTNA Implementation: A Strategic Framework for CISOs
Rolling out Zero Trust Network Access (ZTNA) can feel like a massive undertaking. For CISOs, the challenge isn’t just deploying technology—it’s aligning people, processes, and security principles into a framework that’s both scalable and practical.
Here’s a phased approach that makes ZTNA implementation more manageable while ensuring measurable progress.
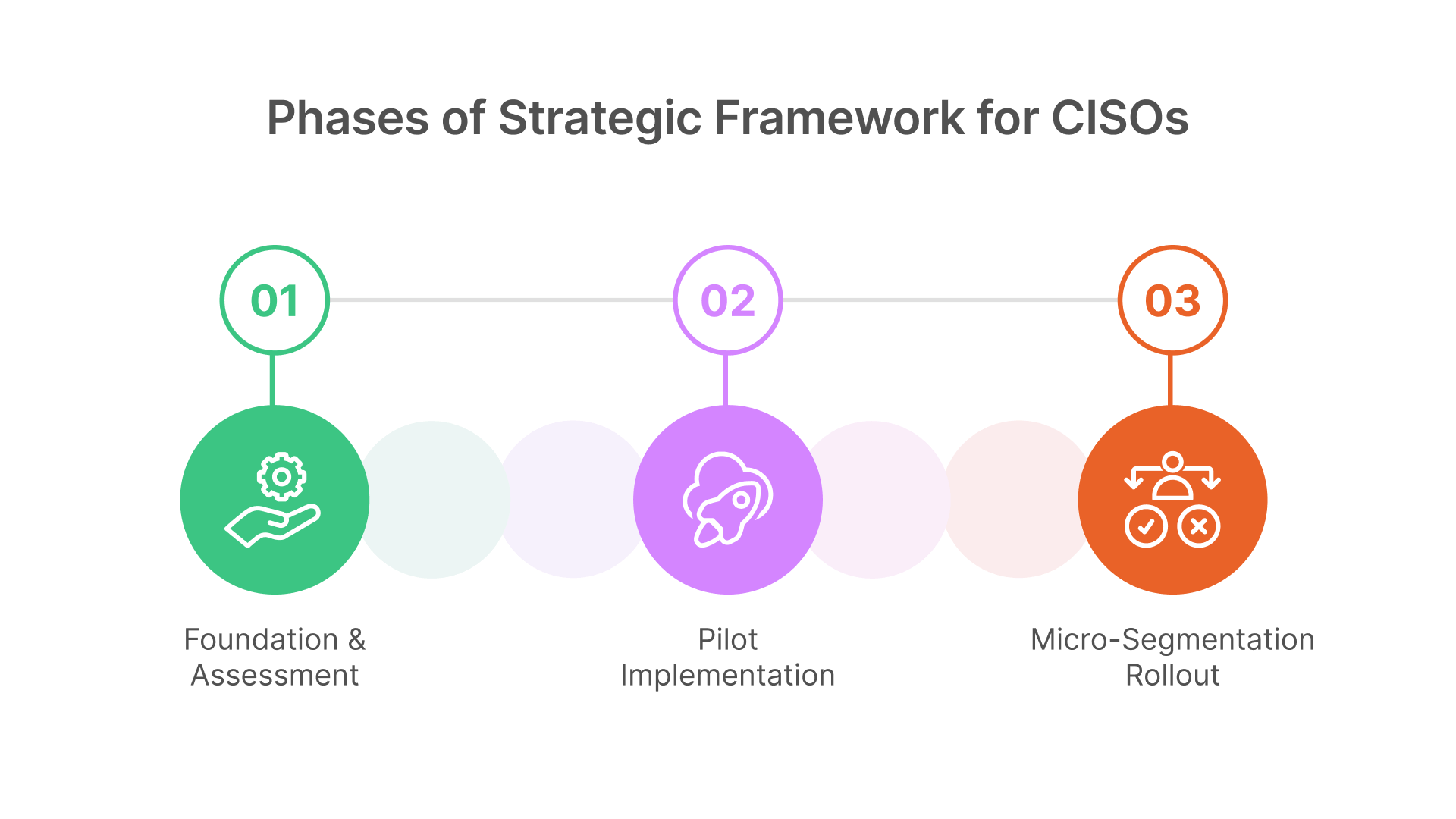
Phase 1: Foundation & Assessment (Weeks 1–4)
Every successful ZTNA journey begins with a strong foundation. This stage is about understanding what you’re protecting and identifying where the risks lie.
- Build your task force: Bring together IT, security, and business leaders to form a dedicated Zero Trust team.
- Inventory applications: Catalog your virtual apps, ranking them by sensitivity and compliance requirements.
- Evaluate vulnerabilities: Assess current remote access pathways and map existing trust relationships.
This baseline provides the visibility you’ll need before rolling out controls.
Phase 2: Pilot Implementation (Weeks 5–8)
Next, it’s time to move from planning to action—but in a controlled way. The goal is to validate Zero Trust principles with a small, diverse test group.
- Pick your pilot apps: Select 2–3 virtual applications with different access needs.
- Deploy ZTNA infrastructure: Set up gateways, connectors, and policy engines, integrated with your identity providers (IdPs).
- Test least-privilege policies: Apply access restrictions with device posture checks to validate the framework.
This phase helps build confidence and uncover operational challenges before scaling.
Phase 3: Micro-Segmentation Rollout
Once the pilot proves successful, you can expand by isolating applications into their own secure zones.
- Adopt identity-based segmentation: Move away from static IP-based controls.
- Create micro-perimeters: Place each application in its own protected boundary.
- Enable adaptive enforcement: Use real-time risk scoring to dynamically adjust access.
This stage ensures that even if one application is compromised, the breach won’t spread laterally across your environment.
Why This Framework Works for CISOs
This phased strategy balances security rigor with operational practicality. By starting small, testing policies, and then scaling through micro-segmentation, CISOs can achieve meaningful results quickly while laying the groundwork for long-term Zero Trust maturity.
The bottom line? ZTNA isn’t a one-time project—it’s an evolving security posture that adapts to your business.
Thinfinity Workspace: Clientless ZTNA for Virtual Applications
Delivering secure access to virtual applications no longer has to mean installing complex clients on every device. With Thinfinity Workspace on Oracle Cloud Infrastructure (OCI), Zero Trust principles are applied seamlessly through a fully clientless experience.
Clientless Browser Access
Users don’t need to download or maintain endpoint software—applications launch directly in the browser. Each session runs in an isolated environment, preventing local malware from spreading into the corporate network. This approach also unlocks true BYOD flexibility, enabling employees and contractors to access virtual apps securely from unmanaged devices without compromising compliance.
Identity Federation & Continuous Authentication
Thinfinity Workspace integrates with leading identity providers such as Okta, Azure AD, and Google Identity, ensuring centralized control and streamlined single sign-on. Multi-factor authentication (MFA) is enforced by default, while continuous authentication goes beyond the login event, verifying identity and device posture throughout the entire session. The result is stronger protection against compromised credentials and unauthorized access.
OCI-Native Security & Scaling
Because it runs natively on Oracle Cloud Infrastructure, Thinfinity Workspace leverages OCI Network Security Groups for fine-grained micro-segmentation. Scaling is handled by Thinfinity Cloud Manager, which automatically provisions and balances resources based on real demand. Enterprises can expand globally with multi-region deployments, enhanced by GeoIP access controls to meet residency and compliance requirements.
A VPN Alternative for Hybrid Enterprises
By combining clientless delivery, strong identity integration, and OCI-native automation, Thinfinity Workspace offers a cloud-first security model that eliminates the need for traditional VPNs. It’s purpose-built for hybrid enterprises that want to simplify remote access while embracing the full benefits of Zero Trust Network Access.
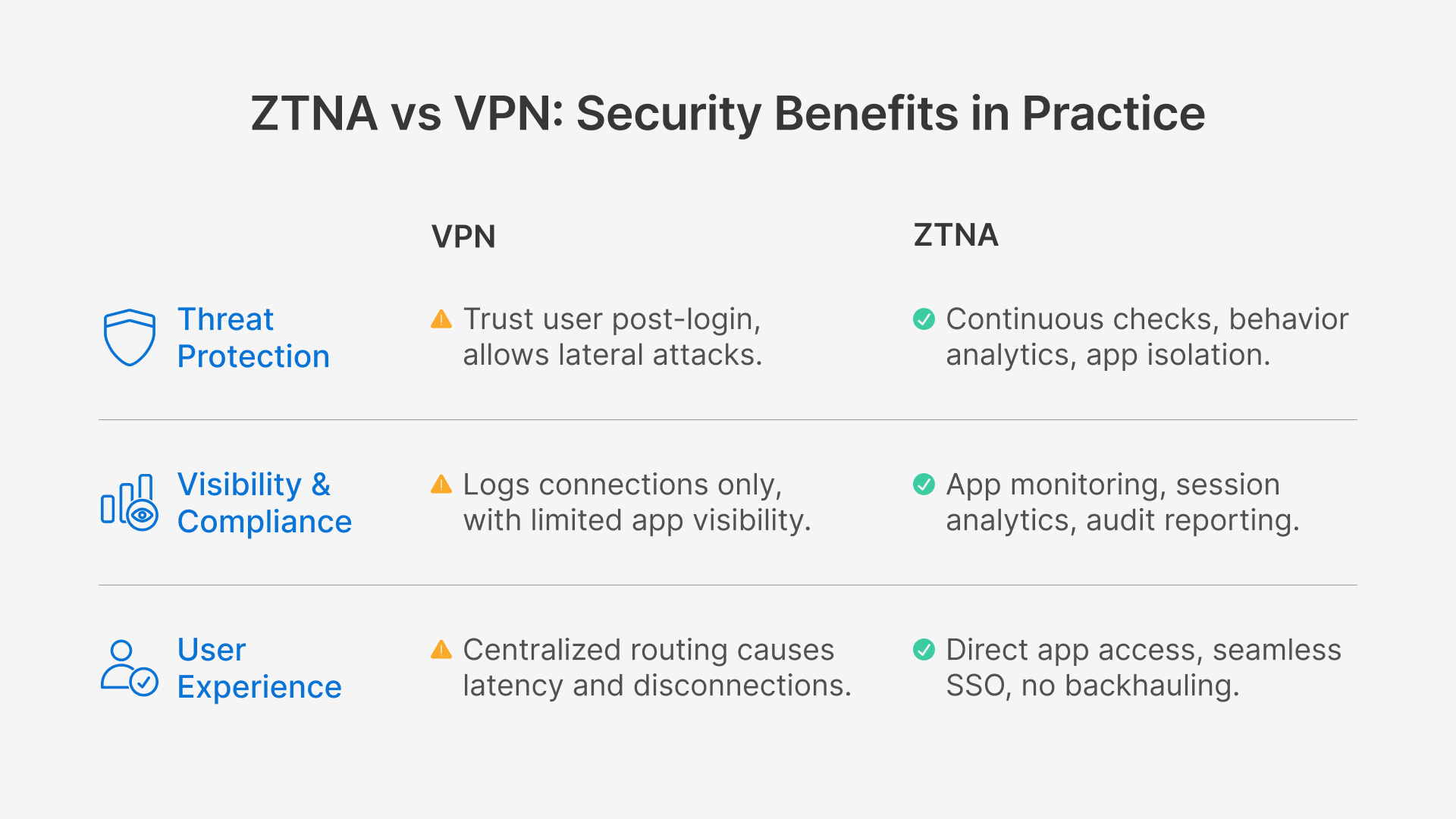
ZTNA vs VPN: Security Benefits in Practice
Zero Trust Network Access (ZTNA) offers a modern alternative, built around continuous verification and application-specific controls. Instead of extending broad network access, ZTNA connects users directly to the resources they need—nothing more, nothing less.
The table below highlights the practical differences between ZTNA and VPN, focusing on security, compliance, and user experience.
Implementation Best Practices for CISOs
For CISOs, implementing Zero Trust Network Access (ZTNA) effectively requires more than just technology—it begins with securing executive sponsorship to position ZTNA as a business enabler rather than IT overhead, followed by controlled pilots that validate principles on non-critical applications before scaling enterprise-wide. Integrating ZTNA with the existing security stack—SIEM, EDR, and SOAR—ensures holistic monitoring, while continuous user education drives adoption and reduces friction. Success should be measured with metrics like Mean Time to Detect (MTTD), incident reduction, and compliance improvements. According to Gartner, organizations that embraced Zero Trust saw 35% lower breach costs and 50% faster detection times, underscoring why CISOs who implement these best practices not only strengthen resilience but also deliver measurable business value.
The Future of Secure Virtual App Access
As hybrid work cements itself as the default operating model, organizations that implement Zero Trust for virtual applications will:
- Enable Secure Innovation – Protect sensitive workloads while empowering flexible work.
- Ensure Compliance – Meet GDPR, HIPAA, and SOX requirements with built-in audit trails.
- Scale Security Dynamically – Adapt policies and controls as threats evolve without re-architecting.
Zero Trust for virtual applications is not optional—it’s the future of enterprise security. CISOs that lead this transition today will safeguard business resilience, regulatory compliance, and long-term competitive advantage.
Frequently Asked Questions (FAQ)
1. What is the biggest security risk of VPNs in hybrid work?
VPNs provide broad, network-level access after login, making lateral movement easy for attackers if credentials are compromised.
2. How does Zero Trust improve security for virtual applications?
3. What’s the difference between ZTNA and VPN for user experience?
4. How can CISOs measure ZTNA success?
Key metrics include reduced incidents, lower breach costs, faster threat detection, and improved compliance audit readiness.