A multi-layered security shield concept symbolizes the “Zero Trust” approach of assembling end-to-end defenses. Modern enterprises require such comprehensive protection for remote and cloud access.
Security Challenges in Hybrid and Multi-Cloud Environments
The rise of hybrid work and multi-cloud infrastructure has stretched traditional IT security models to a breaking point. Employees now access corporate applications from anywhere, often outside the corporate network, and data resides across on-premises data centers and multiple clouds. In this environment, perimeter-based defenses (like VPNs and classic firewalls) are insufficient. In fact, traditional VPN and firewall-centric models are struggling to protect today’s distributed workforce and hybrid IT environments. Attackers exploit VPN vulnerabilities and stolen credentials to move laterally within corporate networks, and unsecured home or public networks pose new risks. Organizations face a critical need for end-to-end security – ensuring that from the user’s device all the way to corporate applications and data, every layer is secured and verified.
Modern security frameworks emphasize a “never trust, always verify” mentality, known as Zero Trust Architecture (ZTA). Instead of implicitly trusting devices or network locations, Zero Trust requires continuous authentication, authorization, and validation of context for each user and session. This approach aligns well with hybrid and multi-cloud realities, where resources are spread out and traditional network boundaries are blurred. End-to-end security built on Zero Trust principles means every access request is treated as potentially hostile until proven otherwise. The challenge for businesses is implementing these principles in a practical, user-friendly way that doesn’t hinder productivity.
End-to-End Security Principles and the Zero Trust Approach
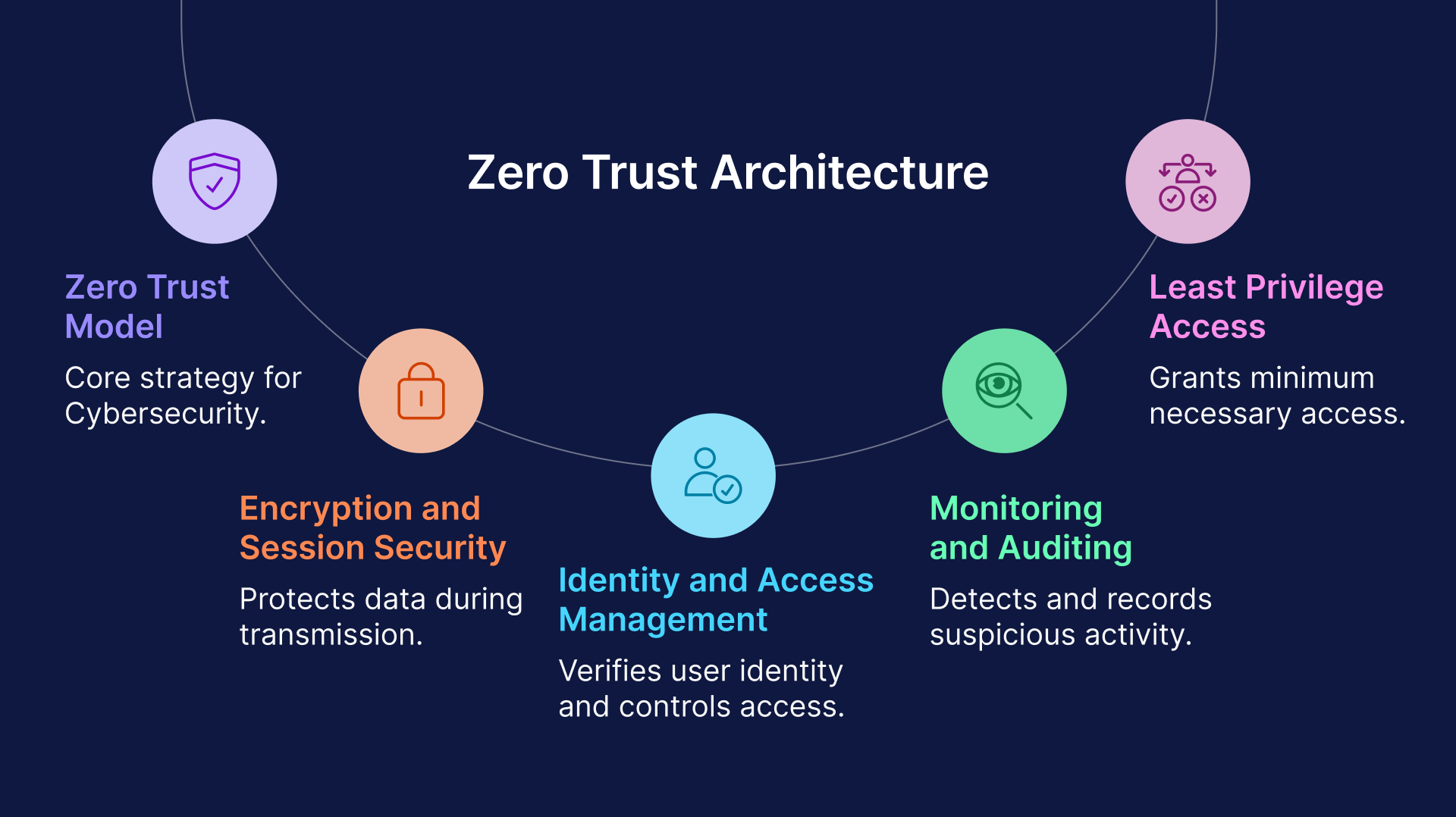
Achieving end-to-end security in a modern IT environment involves several core principles. First is comprehensive identity and access management – verifying that the person or system requesting access is who they claim to be, through strong authentication and strict access controls. Second is least privilege access, ensuring users only get the minimum level of access required to perform their job (for example, an employee might access a specific application but nothing else on the server). Third is encryption and session security, protecting data in transit and preventing eavesdropping or tampering on remote sessions. Finally, continuous monitoring and auditing of sessions is key, so that any suspicious activity can be detected and recorded for forensic analysis.
These principles are embodied in the Zero Trust model, which has rapidly become the preferred strategy for end-to-end cybersecurity. Under Zero Trust, the network is treated as hostile by default; no user or device is inherently trusted, and strict verification is enforced at every step. For example, even if a user is inside the corporate network, they must still authenticate and be authorized for each resource they access. Likewise, simply connecting via a VPN is no longer enough – the system should continuously ensure the user’s legitimacy and enforce policies such as device security posture or time-of-day restrictions.
Thinfinity Workspace is a remote access platform designed with these exact principles in mind. It provides a secure, cloud-ready Virtual Desktop Infrastructure (VDI) and application delivery solution that implements Zero Trust end-to-end. In the following sections, we will explore how Thinfinity Workspace addresses each layer of security – from network access, to identity verification, to session protection and audit – to meet the challenges of hybrid and multi-cloud environments.
Thinfinity Workspace: A Zero Trust Platform for Secure Remote Access
Thinfinity Workspace is an advanced remote workspace and virtualization solution that enables users to access Windows, Linux, and web applications through a browser, without needing traditional VPN clients or desktop RDP setups. It was built by Cybele Software with a “Zero Trust Network Access” (ZTNA) philosophy at its core. In practice, this means Thinfinity enforces strict identity verification and granular access controls for every session, rather than granting broad network privileges. The platform is clientless (accessed via standard web browsers) and uses an agent/gateway architecture to broker secure connections. This modern design contrasts with legacy remote access, which often required opening network ports or installing heavyweight clients.
By embracing a Zero Trust architecture, Thinfinity Workspace ensures that no one can connect to a resource without passing multiple security checkpoints. For example, an administrator can publish a set of cloud-hosted applications or desktops through Thinfinity, and users must authenticate (with possible multi-factor methods) to the Thinfinity portal. Only after verification can they launch the specific app or desktop, and even then, the internal server hosting that resource remains hidden from direct access on the internet. This approach dramatically reduces the attack surface while providing a smooth user experience. As Cybele Software notes, Thinfinity Workspace offers secure remote access with granular policy enforcement and seamless identity management – all “without the complexity of legacy VPNs”. In essence, it delivers the convenience of cloud VDI with security built in from the ground up.
Below, we delve into the key cybersecurity capabilities of Thinfinity Workspace and how each contributes to an end-to-end secure remote access solution.
Zero Trust Network Access (ZTNA)
A cornerstone of Thinfinity’s security model is its implementation of Zero Trust Network Access (ZTNA). Traditional VPNs connect a user’s device into a corporate network, potentially exposing large segments of the network if that device is compromised. Thinfinity takes a far more granular and safer approach. No direct network access is ever granted to end-users – instead, Thinfinity acts as a broker that only allows authenticated users to reach the specific applications or desktops they are authorized for.
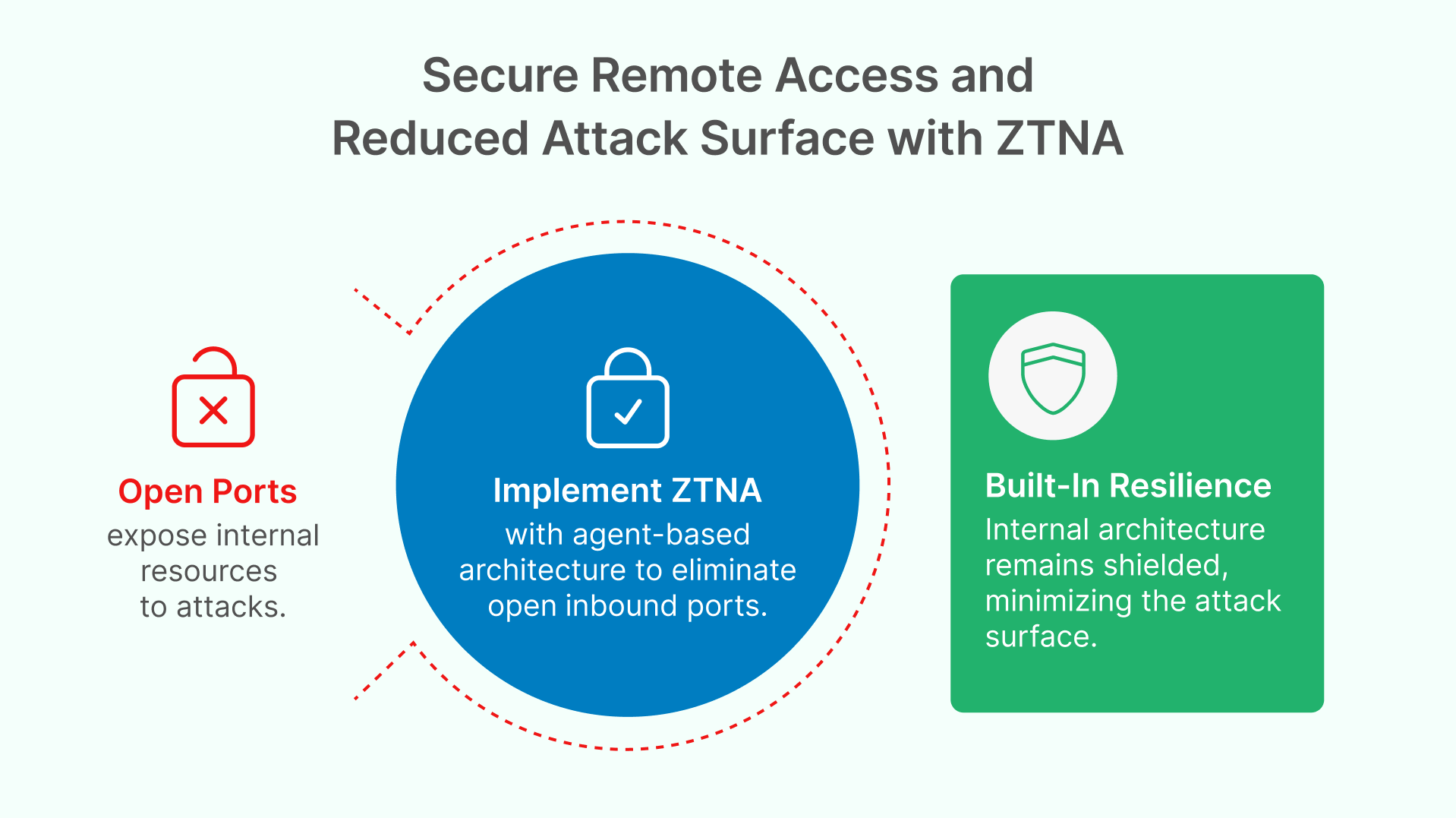
Agent-Based Connectivity: Thinfinity Workspace uses a clever agent-based architecture to avoid exposing any internal network ports. A small agent on the target network (where the application or desktop resides) will only initiate outbound connections to the Thinfinity gateway or broker. This means from the outside, there are no open inbound ports and no public IP addresses pointing directly to internal resources. Corporate firewalls do not need to be opened up for inbound traffic – the Thinfinity agent reaches out to the cloud gateway using an outbound TLS connection, and all user sessions are tunneled through that secure channel. The result is zero public exposure of RDP, SSH, VNC or other protocol ports, eliminating the risk of port scanning, brute-force attacks, and exploits like the infamous BlueKeep RDP vulnerability. All communication is encrypted with strong TLS, and the protocol details are encapsulated so attackers cannot even detect what protocols might be in use.
This ZTNA approach inherently minimizes the attack surface for remote access. An unauthorized person scanning the company’s network from outside would find no indication that remote desktop services even exist, because Thinfinity presents no obvious openings. Meanwhile, legitimate users who authenticate through Thinfinity’s web portal are dynamically granted access to their specific resources and nothing more. This aligns perfectly with Zero Trust principles: only authenticated, authorized users can initiate sessions, and everything is verified on a per-session basis. If a user’s account is revoked or their session time window expires, the access disappears automatically.
In practice, Thinfinity’s ZTNA means companies can retire risky VPN endpoints. There’s no need to place servers in a DMZ or assign them public IPs accessible from the internet. The internal architecture remains shielded, and Thinfinity handles the secure bridging of sessions from outside to inside. This not only improves security but also simplifies network configuration (no complex VPN client setups or network routing issues). According to Thinfinity’s documentation, it’s a “secure architecture that enables SSL web access without any open ports,” embodying Zero Trust security for cloud VDI.
Conclusion Chapter 1
Today’s hybrid and multi-cloud realities require more than legacy VPNs and firewalls. Thinfinity Workspace answers this challenge with a Zero Trust model—verifying every user, locking down access, and securing every session. The result? Stronger security, smoother compliance, and a seamless remote experience.
In Chapter 2, we’ll cover:
- Advanced multi-factor authentication (MFA) and passwordless login
- Integration with enterprise identity providers (SSO, SAML, OAuth)
- Just-in-time and time-based privileged access (RPAM)
- Granular session controls for data loss prevention and device security
- Automated onboarding/offboarding and role management
- Session recording and real-time auditing for compliance
- Tangible business benefits: compliance, operational efficiency, and risk reduction
If you are a CIO, CISO, IT manager, system administrator, or business owner looking to secure remote access and modernize your infrastructure—don’t miss Part 2. We’ll show you how Thinfinity Workspace delivers real-world value for every role.


