Unlocking the Full Potential of Zero Trust with Thinfinity Workspace
In Part 1, we examined why traditional security models are no longer sufficient for today’s hybrid and multi-cloud enterprises. We explored the critical shortcomings of legacy VPNs and firewalls, highlighted the rise of Zero Trust Architecture, and demonstrated how Thinfinity Workspace provides a secure, streamlined alternative for remote access and application delivery. The key message is clear: end-to-end security, built on continuous verification and granular control, is now an operational imperative.
But understanding the need for Zero Trust is only the beginning. In this section, we shift from principles to practice—unpacking the advanced features and concrete outcomes that make Thinfinity Workspace a standout solution for security-conscious organizations.
In Part 2, we’ll dive deeper into:
- Next-generation authentication, including MFA and passwordless access
- Seamless integration with enterprise identity platforms
- Just-in-time privileged access and granular session controls
- Automated user management and powerful auditing capabilities
- Real business value: from compliance to operational efficiency
Whether you’re a CIO, CISO, IT manager, sysadmin, or business owner, Part 2 will show you exactly how Thinfinity Workspace turns Zero Trust theory into secure, practical results for your organization.
Thinfinity Workspace: A Zero Trust Platform for Secure Remote Access
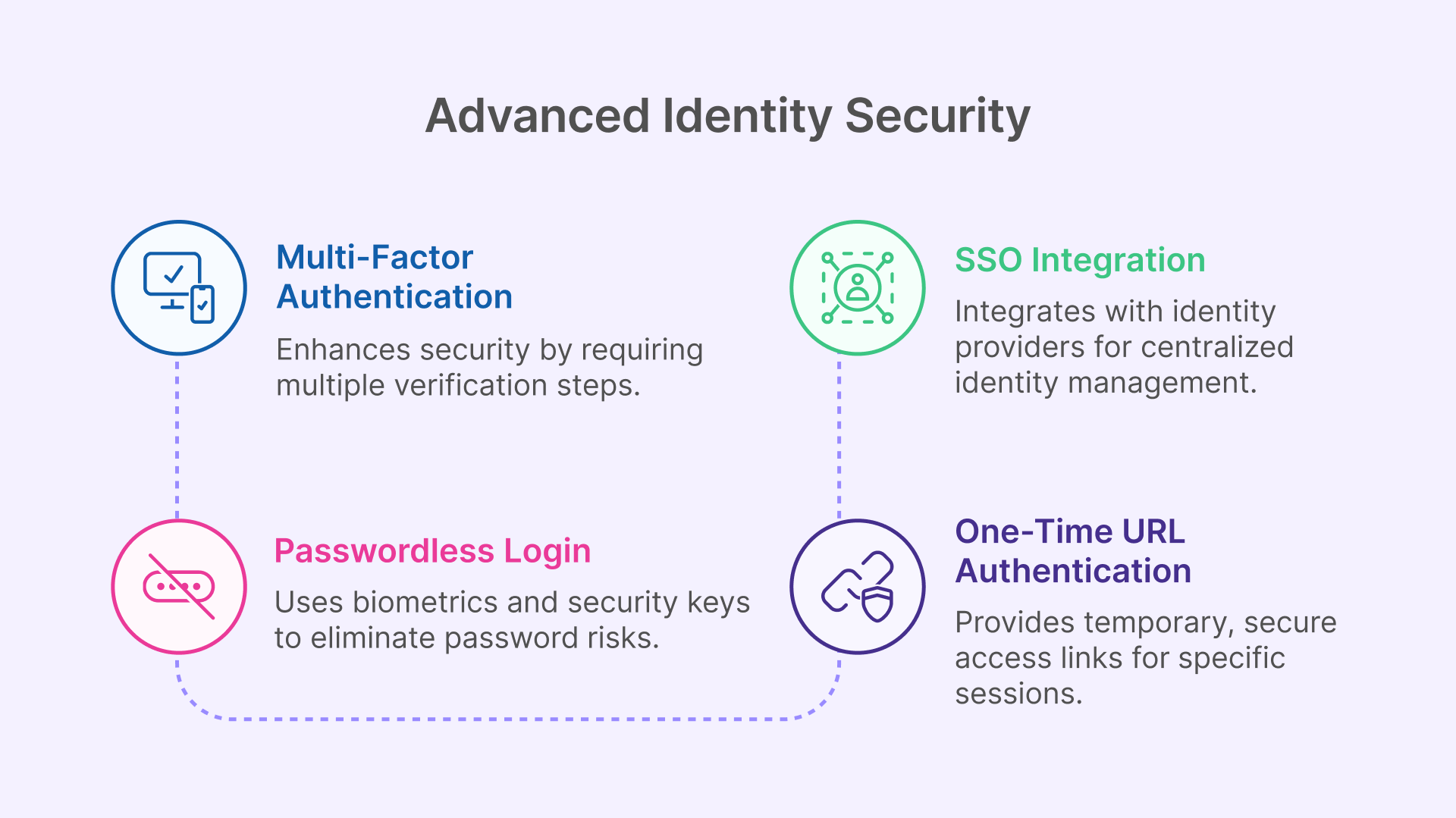
Strong Authentication: MFA and Passwordless Login
Even the best network architecture fails if an attacker can easily steal or guess a user’s password. That’s why multi-factor authentication (MFA) and passwordless login options are critical components of Thinfinity Workspace’s end-to-end security. Right out of the box, Thinfinity supports a range of MFA methods to ensure that only legitimate users gain access. Administrators can integrate Time-based One-Time Password (TOTP) apps like Google Authenticator, Microsoft Authenticator, Duo Mobile, or Okta Verify, adding a second verification step that changes every login. This means even if a password is compromised, an attacker cannot login without the one-time code from the user’s device.
Thinfinity Workspace also integrates with enterprise Identity Providers (IdPs) via SAML 2.0 or OAuth2, including popular services like Microsoft Entra ID (Azure AD), Okta, Ping Identity, and Google Workspace. This allows companies to leverage single sign-on (SSO) and centralized identity management. Users can log in with their existing corporate credentials, and Thinfinity will honor group memberships or attributes from the IdP to determine access rights. This integration not only improves security (through centralized policy and maybe conditional access rules in the IdP), but also enhances user convenience – fewer passwords to remember and a seamless login experience.
In line with modern authentication trends, Thinfinity Workspace 8 introduced passwordless authentication via Passkeys. This feature supports FIDO2 security keys and biometrics (e.g. fingerprint or facial recognition) as login methods. Users can authenticate with a hardware key like YubiKey or with their device’s built-in biometric (Windows Hello) instead of a password, drastically reducing phishing risks. Under the hood, these methods use public-key cryptography and store credentials in secure hardware (such as the device’s TPM for Windows Hello). For organizations with high security requirements, Thinfinity even supports smart card authentication and PKI certificates for login – ensuring compliance with regulations that mandate certificate-based auth.
Another innovative capability is One-Time URL Authentication, which Thinfinity offers to streamline certain workflows. An admin or helpdesk agent can generate a time-limited, unique access link that a user can click to be automatically logged into a specific remote app or desktop. Each One-Time URL is valid for only one session and expires after use, preventing reuse or sharing. This is particularly useful for scenarios like support sessions or third-party vendor access: you can embed these one-click links in a portal or ticket, and the user gets in without needing a permanent username/password at all. It’s a controlled, ephemeral access method that enhances security by eliminating shared credentials and tightly limiting the access scope and duration.
By combining MFA, SSO integration, passwordless tech, and one-time links, Thinfinity Workspace addresses the identity side of security thoroughly. These measures significantly lower the risk of account compromise. According to industry studies, implementing MFA can block over 99% of automated attacks on accounts, and passwordless methods further neutralize phishing. Thinfinity’s approach ensures that identity is the new perimeter – only verified users can even begin to access the system.
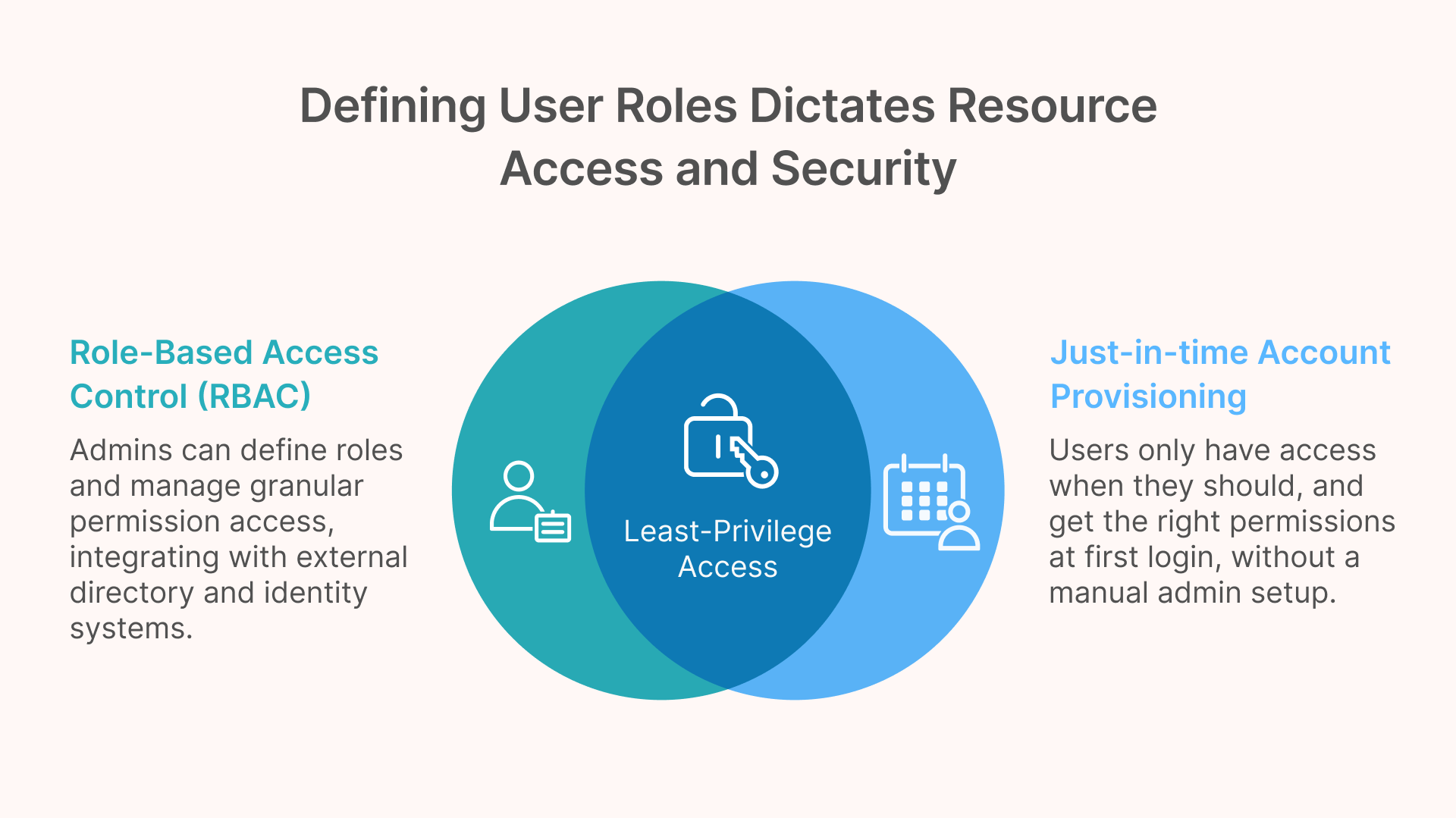
Role-Based Access Control (RBAC) and Least-Privilege Governance
Once a user’s identity is verified, the next question is: what resources should they have access to? Thinfinity Workspace tackles this with robust Role-Based Access Control (RBAC) and granular permission management. Administrators can define roles (such as Regular Employee, Contractor, IT Administrator, etc.) and assign permissions to those roles regarding which desktops, applications, or data the role can access. Every user session is governed by these assigned roles, enforcing a least-privilege model. For example, a finance department user might only see accounting applications and not be allowed to launch engineering or HR systems. This containment dramatically limits the damage that can be done if an account is compromised – the attacker would only see a narrow slice of the environment.
Thinfinity makes RBAC easier to manage by integrating with external directory and identity systems. It supports mapping users and groups from Active Directory or SAML/OAuth2 IdPs (like Azure AD, Okta, etc.) to internal Thinfinity roles. This means you can tie Thinfinity’s access control to your existing organizational structure. If a user is part of the “Contractors” group in Okta, for instance, Thinfinity can automatically map them to a Contractor role which has restricted access. The platform even provides flexible rule-based mappings, where you can automatically assign roles based on user attributes (department, group membership, email domain, and so on).
A particularly powerful feature is Just-In-Time account provisioning and auto-deprovisioning. When Thinfinity is linked to an IdP, it can be configured such that if an authenticated user logs in and no local Thinfinity account exists yet, the system will auto-create an account on the fly and assign the appropriate role. This auto-provisioning means new employees or partners get access immediately based on their directory status, with no manual admin setup required. It also implies that if someone is removed from the corporate directory (e.g. upon leaving the company), they lose Thinfinity access too, maintaining a single source of truth. Thinfinity’s documentation highlights that this seamless onboarding/offboarding aligns with dynamic workforce needs and Zero Trust, by ensuring users only have access when they should, and get the right permissions at first login.
All these mappings and automatic role assignments feed into centralized policy management. Administrators can adjust a role’s permissions or the mapping rules in one place, and it instantly affects all users in that role. This makes it much simpler to enforce organizational changes (like a reorg or merger) without touching individual accounts.
The net effect is strong governance: every action through Thinfinity is tied back to an identity and a role, and no user can step outside their permitted boundaries. This greatly aids in implementing the principle of least privilege and separation of duties. If auditors ask “who can access Server X or sensitive App Y?”, Thinfinity’s RBAC makes it easy to answer and shows that only the appropriate role can, with all actions logged.
Understand Our RBAC Implementation →
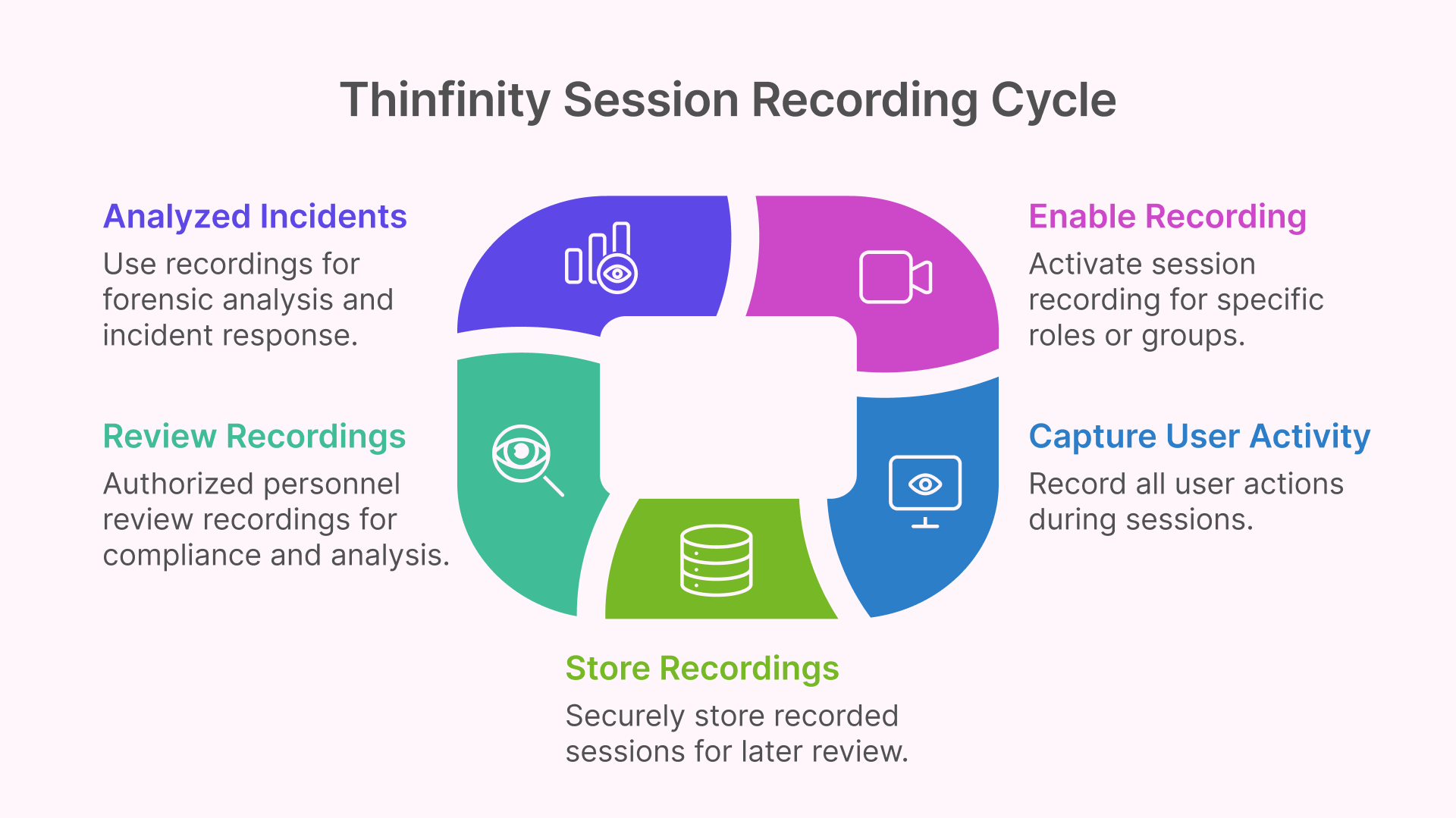
Session Recording and Auditing for Accountability
For sensitive operations and compliance requirements, being able to monitor and review what happens during a remote session is essential. Thinfinity Workspace includes a secure session recording capability for remote desktop sessions. Administrators can enable full video recording of user sessions on published desktops or applications. Every mouse movement, screen update, and keystroke can be captured in the recording, creating a comprehensive audit trail of user activity. This is invaluable for forensic analysis in case of an incident, or simply for routine compliance auditing in industries like finance and healthcare.
Thinfinity allows granular control over which sessions get recorded. You might not need to record every user’s activity (and indeed, privacy considerations mean you should only record what’s necessary). With Thinfinity, you could choose to record sessions for specific high-privilege roles or groups – for example, record all sessions of contractors, or IT administrators, or any user accessing a particularly sensitive system. This role-based activation ensures you capture the most critical interactions without overwhelming storage or invading privacy for regular tasks. The recordings themselves can be stored securely and accessed by authorized personnel for review.
From a business standpoint, session recording serves multiple purposes. It helps with compliance – many standards (PCI DSS, ISO 27001, SOC 2, etc.) require monitoring of administrative access or critical transactions, and having video logs meets those controls. It also acts as a deterrent against misuse: users aware that their session is being recorded are less likely to attempt malicious or unauthorized actions. In the event something does go wrong, the recorded footage provides an exact replay of events, which can speed up incident response and root cause analysis.
Thinfinity’s session recording is part of its broader auditing and logging framework. In addition to video, the system logs user logins, resource launches, file transfers, etc. This ties into the concept of end-to-end security by ensuring visibility and accountability at the final stage of the chain – after a user has been authenticated and authorized, their actions are not invisible. Everything is trackable if needed. Such capabilities usually require separate tools in a traditional RDP or VPN setup, but Thinfinity builds it into the platform for a one-stop solution.
Discover Security & Monitoring Features →
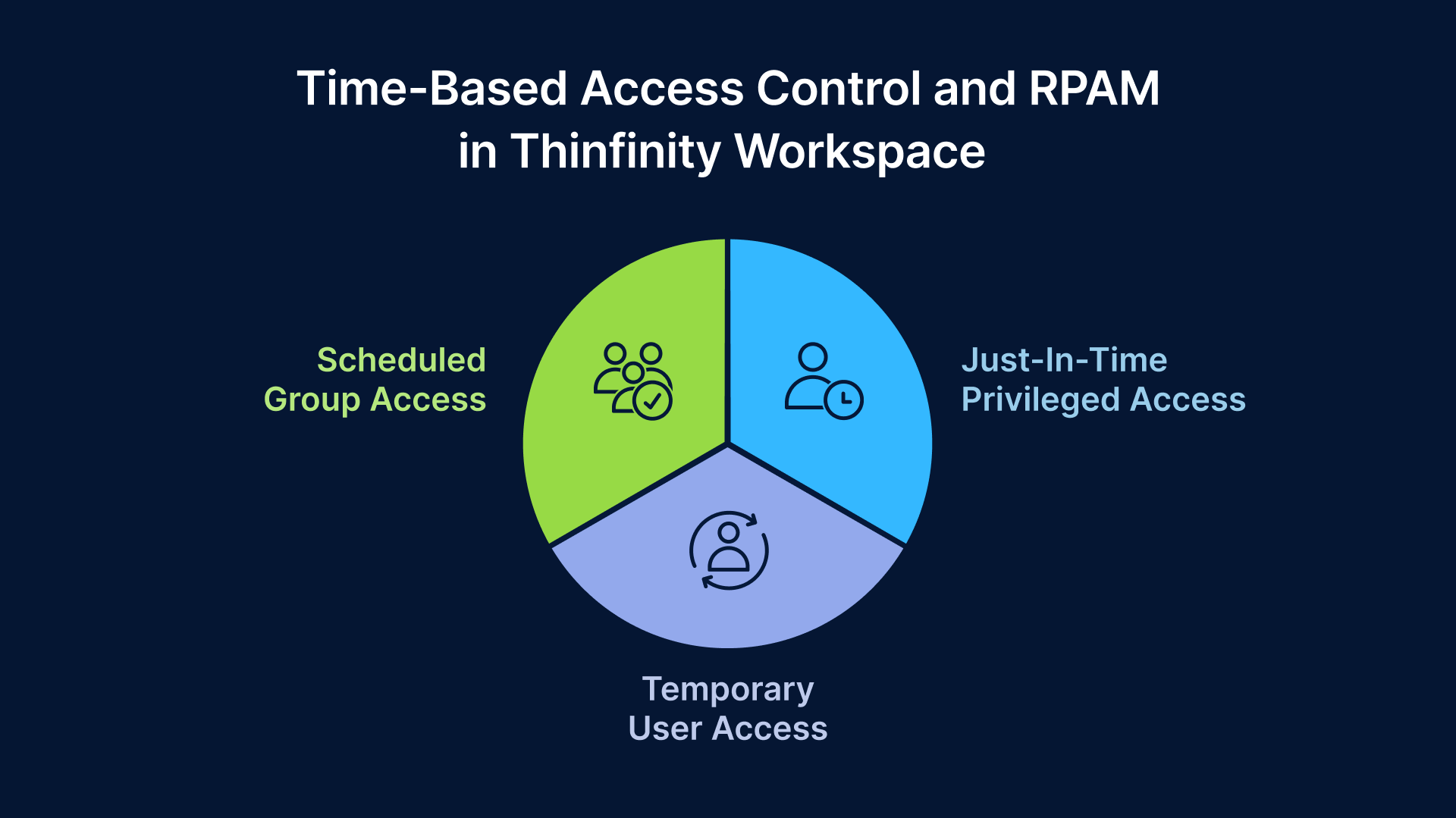
Time-Based Access Controls and Privileged Access Management (RPAM)
A dynamic aspect of security that Thinfinity Workspace handles adeptly is time-based access control and Remote Privileged Access Management (RPAM). Not all users should have 24×7 access to resources, especially highly sensitive ones. Thinfinity lets administrators put very fine-grained schedules on when and for how long access is allowed. For example, you can define allowed access windows (say, weekdays 9am–6pm) for specific users, groups, or resources. If someone tries to connect outside their allowed hours, Thinfinity will block it. This is a simple but powerful mitigator of risk – even if an attacker obtained credentials, they cannot use them at an odd hour if policy disallows it. Thinfinity can even auto-terminate active sessions that run past the approved time window, preventing after-hours persistence.
For third-party vendors or support engineers, Thinfinity supports temporary access provisioning. You might only want to let an outside contractor onto a server during a scheduled maintenance window. With time-based rules, you can set that vendor’s account to be valid only during a specified period (e.g., access opens at 10:00 and closes at 14:00 on a certain day). After that, the access is automatically disabled. This significantly reduces the risk of forgetting to turn off a vendor account – a common oversight that can lead to unintended backdoors.
Thinfinity’s approach to Remote Privileged Access Management (RPAM) extends this concept specifically to privileged users (like admins). It enables Just-In-Time (JIT) privileged access, meaning administrators or high-privilege accounts do not have standing access by default; instead, they are granted elevated access only for the specific duration and task needed. For example, an IT admin might “check out” access to a production server for a 2-hour window to perform updates, after which that access automatically expires. This ties into a broader security best practice of eliminating permanent privileged accounts – you have zero standing privilege until it’s approved for a short time. Thinfinity facilitates this by allowing users to “book” access to sensitive resources for a pre-approved timeframe. Outside of that reservation, the system will not allow the connection, and once the window ends, access is deprovisioned immediately.
Crucially, Thinfinity includes approval workflows for such privileged access requests. An administrator’s request to access a critical server could be made to require a manager’s or security officer’s approval through the platform before it activates. This ensures oversight and that at least two people are aware of any highly privileged activity (a key component in mitigating insider threats).
Additionally, you can enforce per-resource access schedules. For instance, a particularly sensitive database server might only be made available via Thinfinity during business hours, regardless of who’s trying to access it. Thinfinity will enforce those resource-specific schedules automatically. It also supports a degree of self-service for users, where a user can request or schedule their own access within policy bounds, possibly getting automated approval if criteria are met. This reduces the administrative burden while still keeping tight control.
By implementing time-based restrictions and just-in-time access, Thinfinity Workspace ensures that even if credentials are stolen or misused, the window of opportunity for attackers is drastically narrowed. It also addresses compliance requirements found in standards like ISO 27001 or NIST guidelines, which recommend limiting the time frame of privileged access. Overall, these features add a temporal dimension to Zero Trust – not only do you verify who and what is accessing, but also when, making sure the timing aligns with expected patterns.
Learn more about the Resource Reservation module →
Browser-Based Session Security and Device Redirection Controls
Thinfinity Workspace is a browser-based solution, which means users interact with their remote desktops or applications through an HTML5 web interface. This approach has security benefits on its own (no heavy client to keep patched, no direct network connectivity from the endpoint to the server), but Thinfinity goes further by giving administrators detailed controls over the in-session behavior and device integration. Essentially, it allows companies to fine-tune the balance between security and user convenience within the remote session.
Granular Session Policies: Admins can enable or disable various features like clipboard, file transfer, printing, audio, and USB device redirection on a per-user or per-resource basis. For example, you might disable clipboard copy-paste and file transfers for a highly sensitive finance application, preventing users from easily exfiltrating data. Alternatively, you could allow file transfers but then restrict specific file types (e.g., block .exe or .bat files to prevent moving executables). Thinfinity even offers an Intermediate Virtual Disk (“ThinDisk”) that can be toggled on, which serves as a controlled buffer for file exchange between the remote session and the local device. Policies can dictate whether files placed in this virtual disk auto-download to the user’s machine or not. By adjusting these knobs, organizations can enforce data loss prevention policies—like “no downloads from system X”—while still allowing legitimate use (e.g., maybe allow download of only PDF reports but not raw data files).
Device Redirection: In many remote desktop scenarios, users want to print documents or play audio from the remote system on their local device. Thinfinity supports these needs with control. Printer redirection can be enabled, which allows the remote application to print to the user’s local printer seamlessly. If allowed, Thinfinity’s virtual printer ensures an easy print experience without actually transferring raw print spool files insecurely. Similarly, audio redirection can be enabled or disabled depending on the use case. For instance, in a call center application you might enable two-way audio, while in a sensitive environment you might mute all remote audio to avoid someone using the channel to send out data via text-to-speech or audio cues. Even USB device or peripheral redirection can be managed – Thinfinity can block or permit certain device types if needed (for example, you might block USB storage devices but allow smart card readers).
These browser-based session controls are crucial for compliance and productivity. They ensure that even once a user is connected to an application, the organization still has guardrails on what the user can do with the data. If regulations demand that no data leaves a secure enclave, Thinfinity can enforce that by disabling downloads or clipboard copying from that session. On the other hand, for day-to-day work, you might allow most features to give users a near-local experience. Thinfinity essentially provides the same kinds of controls that traditional enterprise virtual desktop solutions (like Citrix) offer, but through an easier web-based interface.
From a security standpoint, this means browser-based access does not equate to unrestrained access. Every channel (clipboard, disk, print, audio) is a potential data egress or ingress path that Thinfinity lets you manage. And because these policies can be set per user/group or per application, they can be aligned with Zero Trust principles (for example, stricter controls for higher risk scenarios). The end result is a remote session environment that is tailored to your security needs without completely hampering user productivity. In summary, Thinfinity Workspace’s device redirection and session controls give organizations confidence that remote users can’t easily violate data handling policies, whether inadvertently or maliciously.
Learn more about Device and Peripheral Integration →
Business Benefits: Compliance, Operational Efficiency, and Risk Reduction
Deploying a secure end-to-end solution like Thinfinity Workspace isn’t just about checking technical boxes – it also brings tangible business benefits. One major advantage is simplified compliance. Many regulations (GDPR, HIPAA, PCI DSS, etc.) require strict control of data access, strong authentication, audit logs, and data protection in transit. Thinfinity’s integrated security features help fulfill these requirements out of the box. For instance, enforcing MFA and passwordless login helps meet compliance for secure authentication, session recording provides audit trails for regulators, and TLS encryption with no legacy protocols helps satisfy standards like PCI DSS which forbid outdated encryption. As noted in Thinfinity’s guidance, organizations across industries – from finance to healthcare – can use the platform to ensure regulatory compliance while still enabling secure remote access. Having these capabilities built into a single solution means less reliance on multiple point products and easier evidence gathering during audits.
Another key benefit is operational efficiency and cost savings. Traditional VPNs and remote desktop setups come with significant overhead: maintaining VPN hardware/appliances, managing client software on every endpoint, dealing with support tickets for VPN issues, and manually provisioning user accounts or access rules across systems. Thinfinity’s ZTNA model removes the need for VPN appliances and uses cloud-native gateways, often reducing infrastructure costs and complexity. In fact, a comparison of ZTNA vs legacy VPN showed that Thinfinity’s approach lowers infrastructure costs, minimizes maintenance, and reduces the burden on IT. Because it’s clientless, IT staff don’t have to troubleshoot installation on every user’s device – access is through the browser. Features like automatic account provisioning and user self-service for access requests further save administrative time. One could onboard a new remote employee in minutes instead of days, as the Zero Trust access policies and SSO integration handle the heavy lifting. A real-world outcome observed is up to 50% reduction in onboarding time when moving to a modern ZTNA model for remote access.
Risk reduction is, of course, the ultimate goal of these security enhancements, and it carries business value by preventing costly breaches and downtime. By eliminating open ports and reducing the exposed network surface, Thinfinity dramatically lowers the risk of common attacks like RDP brute-force intrusion or malware spread through VPN. Granular RBAC and time-based access mean that even if an account is compromised, the blast radius is limited – attackers cannot roam freely. All these factors contribute to reducing the likelihood and impact of security incidents, which protects the company’s finances and reputation. As an added bonus, a well-implemented Zero Trust remote access solution can actually improve user productivity and satisfaction (fast, seamless access from anywhere) while keeping security tight. This alignment of security and usability is a strategic win for the business: IT isn’t perceived as a roadblock, and users have the freedom to work remotely on any device without endangering the company.
In summary, Thinfinity Workspace’s end-to-end security doesn’t just guard IT assets – it also helps the organization be more agile, cost-effective, and compliant. It reduces the need for multiple disjointed tools (VPN, separate MFA tool, separate session recorder, etc.) by combining functions, which in turn streamlines operations. Enterprises can securely enable remote work while actually lowering IT complexity and overhead. This synergy of security and efficiency is a key reason many organizations are now looking beyond traditional solutions and embracing Zero Trust platforms like Thinfinity.
Thinfinity vs. Traditional VPN/RDP Solutions
It’s useful to compare how Thinfinity Workspace stacks up against the older paradigms of remote access – namely traditional VPN combined with RDP (Remote Desktop Protocol) or other remote desktop tools. The differences are significant:
| Dimension | Thinfinity Workspace (ZTNA, App Virtualization) | Traditional VPN + RDP Solutions | Key Takeaway |
|---|---|---|---|
| Access Model | Granular, Application-Level Access: Users are granted access only to specific apps or desktops for which they are authorized—nothing else. | Network Tunnel, Broad Access: Once connected, the device joins the entire corporate network, exposing all resources the user has network rights to. | VPNs expose the entire network to a single compromised device. Thinfinity grants access only to verified apps and users. |
| Zero Trust Posture | Continuous Zero Trust: Every session and action is authenticated and evaluated (user, device, time, role). No implicit trust is granted. | Implicit Trust on Connection: Access is granted simply by being “on the network,” and all traffic is assumed legitimate. | Thinfinity enforces “never trust, always verify.” VPNs assume trust after login. |
| Client Software Requirement | No Client Needed: 100% clientless browser access from any device. No installs, updates, or VPN key distribution. | Client Software Required: VPN and RDP clients must be installed and patched on every endpoint, increasing friction and IT workload. | Thinfinity lowers support costs and eliminates software distribution headaches. |
| Attack Surface | Reduced Surface: No inbound ports, RDP, or VPN appliances exposed; all connectivity is outbound. Uses HTTPS/WebSockets, obfuscates internal protocols. | High Surface: VPN gateways and RDP servers are frequent attack targets; open ports are exposed to the internet and susceptible to automated attacks. | Thinfinity removes obvious attack vectors. VPN/RDP are routinely exploited. |
| Integrated Security Features | Unified Security Stack: Built-in MFA, SSO, RBAC, session recording, device control, IP restrictions—all managed centrally for consistent policy enforcement. | Fragmented Security: Requires combining separate tools for MFA, PAM, monitoring, etc.; policies are siloed and hard to coordinate. | Thinfinity simplifies compliance and ensures all controls work together. |
| Performance & Scalability | Optimized for Cloud and Hybrid: Scales across cloud regions, supports load balancing, and uses modern protocols (WebSocket, compression) for efficient access. | Legacy Bottlenecks: VPNs can choke under load, force all traffic through a central point, and struggle to support distributed workforces. | Thinfinity ensures low-latency, high-performance access—reducing user frustration and shadow IT. |
| Monitoring & Visibility | Comprehensive Visibility: Centralized audit logs, real-time monitoring, session recording; see who accessed what and when. | Limited Monitoring: Requires additional tools for audit trails; once inside the network, activity may be invisible without extra agents. | Thinfinity accelerates detection and response; VPN/RDP visibility is often incomplete. |
| User Experience | Frictionless Access: Single sign-on, consistent experience via browser, supports BYOD securely. | Cumbersome Process: Multiple logins, inconsistent experiences across devices, risk of version mismatches. | Thinfinity provides modern, seamless access—no more juggling VPN/RDP clients. |
In essence, Thinfinity Workspace can replace traditional VPNs for remote access, providing a more secure and more controlled solution. Legacy VPN/RDP was suitable for an earlier era of IT, but today’s environment demands the kind of fine-grained, identity-centric security that Thinfinity offers. Organizations adopting Thinfinity have found they can decommission legacy remote access infrastructure, reducing costs and closing security gaps. Perhaps most importantly, by limiting access and removing implicit trust, Thinfinity significantly lowers the risk of a catastrophic breach originating from a single compromised remote user – which is a key advantage over the old way of doing things.
Conclusion
The shift to hybrid work and multi-cloud IT has made end-to-end security a top priority. Thinfinity Workspace exemplifies how a modern platform can address this need by weaving together Zero Trust principles, strong authentication, fine-grained access control, and session security into one solution. We’ve seen how Thinfinity’s features – from ZTNA architecture (no open ports, outbound-only connections) to MFA and passwordless logins, from RBAC and just-in-time privileged access to session recording and device control – collectively provide a 360-degree security blanket over remote access operations. This not only protects against external threats and insider misuse, but also helps businesses meet compliance requirements and operate more efficiently.
In comparison to traditional VPN and RDP setups, Thinfinity Workspace offers a clear strategic upgrade: more security, more control, and often less complexity in the long run. It enables companies to embrace cloud VDI and remote work with confidence that security won’t be sacrificed. By implementing an end-to-end security approach using Thinfinity Workspace, organizations in the US, Europe, and beyond can support their modern workforce and cloud-first initiatives while significantly reducing risk and maintaining an upper hand against cyber threats. In today’s threat landscape, that comprehensive, Zero Trust-driven defense is not just an IT improvement – it’s a business imperative for success and resilience.


