As small businesses increasingly depend on remote and hybrid work, managed service providers (MSPs) must deliver secure, scalable, and affordable access to applications and desktops. This checklist helps MSPs build Zero Trust-ready VDI environments, ensuring every session, user, and device is verified — and every client can operate confidently in a modern digital workspace.
1. Enforce Strong Data Access Controls & Protection Layers
Key Actions for MSPs:
- Classify client data by sensitivity and define where it resides across VDI environments.
- Apply least-privilege ZTNA rules, ensuring users only access the specific apps or desktops they need.
- Enforce session-level restrictions (disable copy-paste, USB, and printing) for sensitive workloads.
- Encrypt all traffic between endpoints and virtual desktops, both in transit and at rest.
- Use micro-segmentation to isolate client tenants and prevent lateral movement between customer environments.
- Validate device posture before granting access (anti-malware, OS updates, compliance).
- Provide data isolation for each customer inside your MSP-hosted cloud environment.
2. Strengthen Governance & Approval Workflows
Key Actions for MSPs:
- Maintain a full inventory of hosted applications, virtual desktops, and user groups for each client.
- Establish multi-tenant governance policies — separating client data, credentials, and access rules.
- Require approval workflows for new client accounts, application publishing, or access policy changes.
- Use role-based access controls (RBAC) for MSP admins and client teams alike.
- Detect shadow usage and ensure customers aren’t bypassing secure ZTNA access paths.
- Provide periodic security training and awareness for small-business clients and their teams.
3. Map Regulatory & Compliance Requirements
Key Actions for MSPs:
- Align hosted environments with SMB-relevant regulations (GDPR, HIPAA, SOC 2, ISO 27001, PCI-DSS).
- Provide audit logging and reporting per tenant, covering logins, session durations, and data access.
- Implement data-sovereignty controls — host European clients in EU regions and US clients in US regions.
- Retain activity logs according to customer or regional compliance mandates.
- Verify that your underlying infrastructure (IONOS Cloud) meets recognized compliance standards.
4. Establish Identity, Access, and Monitoring Systems
Key Actions for MSPs:
- Integrate SSO and MFA across all client tenants to unify identity management.
- Continuously monitor session behavior and flag anomalies (new device, foreign IP, large data transfer).
- Enforce device posture validation at the gateway level before granting access.
- Use centralized dashboards to visualize all tenant activity from the MSP console.
- Schedule regular access reviews to revoke dormant accounts and stale privileges.
- Integrate endpoint detection and response (EDR) tools for deeper visibility into client desktops.
5. Build Incident Response & Recovery Plans for Each Tenant
Key Actions for MSPs:
- Develop ZTNA/VDI-specific response playbooks for client environments (credential theft, compromised session, or ransomware event).
- Automate detection and isolation: quarantine compromised desktops or revoke access tokens instantly.
- Implement clean-image recovery to restore services rapidly without spreading infections.
- Maintain customer-specific communication workflows and escalation trees.
- Conduct tabletop exercises with your clients to validate their business-continuity posture.
Summary Table
| Focus Area | Key MSP Actions |
|---|---|
| Data Access & Protection | Least-privilege rules, encryption, micro-segmentation, DLP, device posture enforcement. |
| Governance & Approval | Tenant inventory, RBAC, approval workflows, multi-tenant segregation, security training. |
| Compliance | Map SMB regulations, audit logs, data sovereignty, certified cloud infrastructure. |
| Identity & Monitoring | SSO + MFA, continuous monitoring, dashboards, EDR integration, access reviews. |
| Incident Response | Playbooks, automation, rapid recovery, communication, regular testing. |
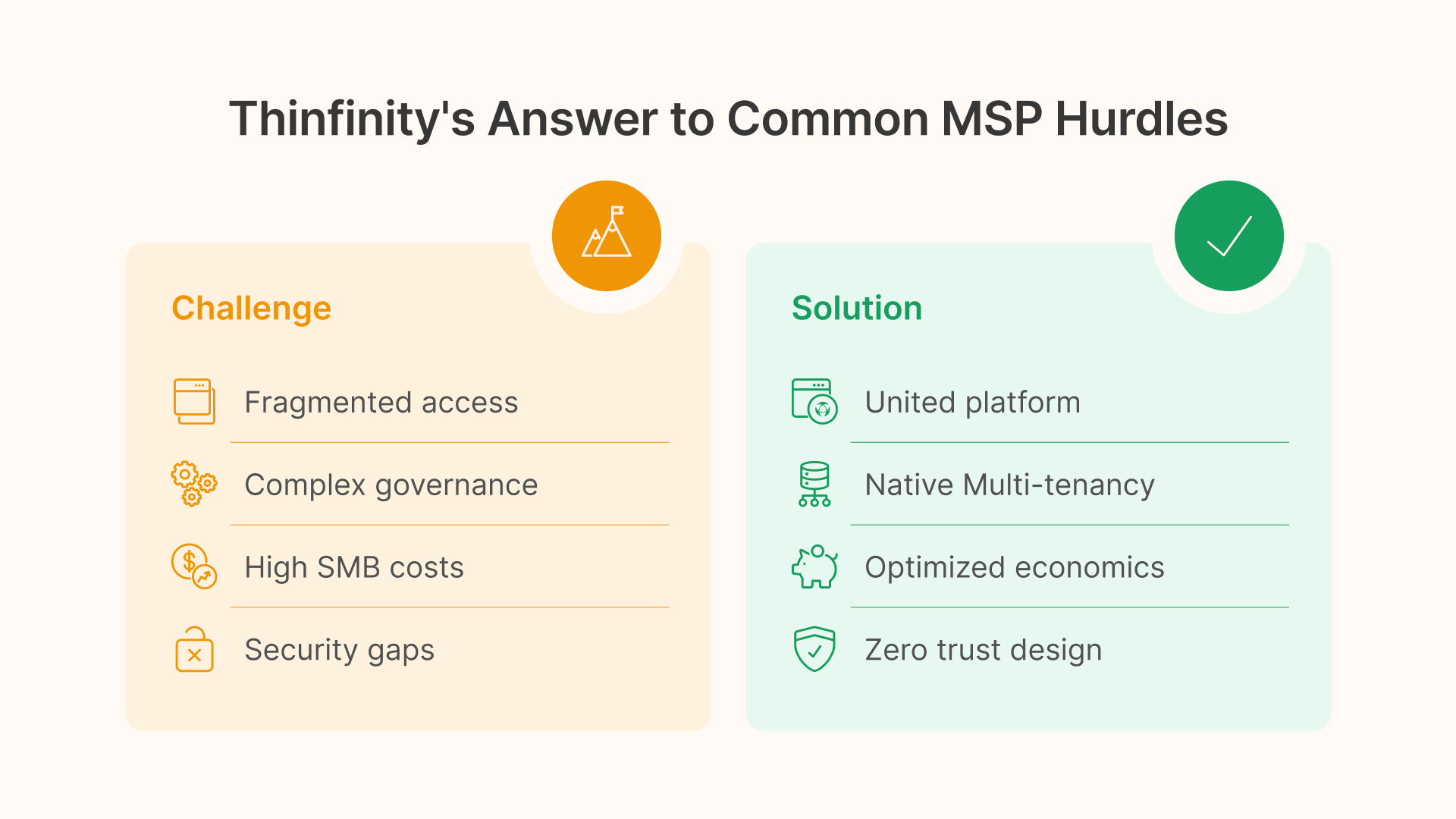
Conclusion — Why Thinfinity on IONOS Cloud Is the Best MSP Platform
For MSPs serving small businesses, managing multiple point solutions for secure access and desktop delivery is costly and complex.
Thinfinity Workspace on IONOS Cloud solves this by combining Zero Trust Network Access (ZTNA) and Virtual Desktop Infrastructure (VDI) in a single, multi-tenant, cloud-native platform.
Why MSPs Choose Thinfinity + IONOS Cloud:
- 🧩 All-in-One Platform: ZTNA and VDI unified under one management console — no VPNs, no separate brokers.
- ☁️ MSP-Ready Multi-Tenancy: Host multiple SMB clients in isolated environments with per-tenant controls and billing.
- 🛡️ Zero Trust by Design: Identity-centric access, MFA, and device posture checks natively integrated.
- ⚙️ Cloud-Native on IONOS: High-performance European datacenters with predictable costs and strong compliance (ISO 27001, GDPR).
- 💸 Optimized for SMB Economics: Efficient resource pooling and flexible pricing models let MSPs deliver enterprise-grade services affordably.
- 🚀 Scalable & Hybrid: Deploy on-premise, in the IONOS Cloud, or hybrid — all under one unified access layer.
In summary:
Thinfinity Workspace on IONOS Cloud is the only unified cloud-native platform that enables MSPs to deliver both secure ZTNA access and full-featured VDI services to small businesses — efficiently, compliantly, and profitably.
It empowers MSPs to future-proof their managed services portfolio, offering small clients enterprise-grade access control, virtualization, and compliance within a single, modern platform.